Industrial control systems are critical to the safe and reliable operation of critical infrastructure companies such as those in oil & gas production, water & wastewater treatment and distribution, transportation and manufacturing. Cyber incidents in industrial control systems constitute a significant threat to safe and reliable operation.
Awareness of the vulnerability of industrial control systems has increased significantly since Stuxnet made the headlines in 2010. Even before Stuxnet was discovered, industrial control system cyber incidents were not uncommon and they are even more common today. Examples include:
- Australia (2000), a disgruntled former contractor used stolen equipment and remotely accessed a wastewater control system multiple times over a period of months and released over 200,000 gallons of raw sewage into the local environment, causing over $1M of damage.
- Ohio (2003), a malware called Slammer worm penetrated the control systems network at the Davis-Besse nuclear power plant and disabled a safety monitoring system for nearly five hours.
- Poland (2008), a teenager used a homemade device to cause train derailments and other incidents in the city of Lodz, resulting in 12 injuries.
- Texas (2012), a hacker remotely gained unauthorized access to a water treatment control system and published the details online.
- Germany (2014), the blast furnace at a steel mill suffered massive damage after hackers gained access to the control system network and disrupted the control and safety systems.
- Ukraine (2015), approximately 80,000 homes in the Ivano-Frankivsk region in Ukraine were left without electricity for six hours after hackers infiltrated the control system network of a power company.
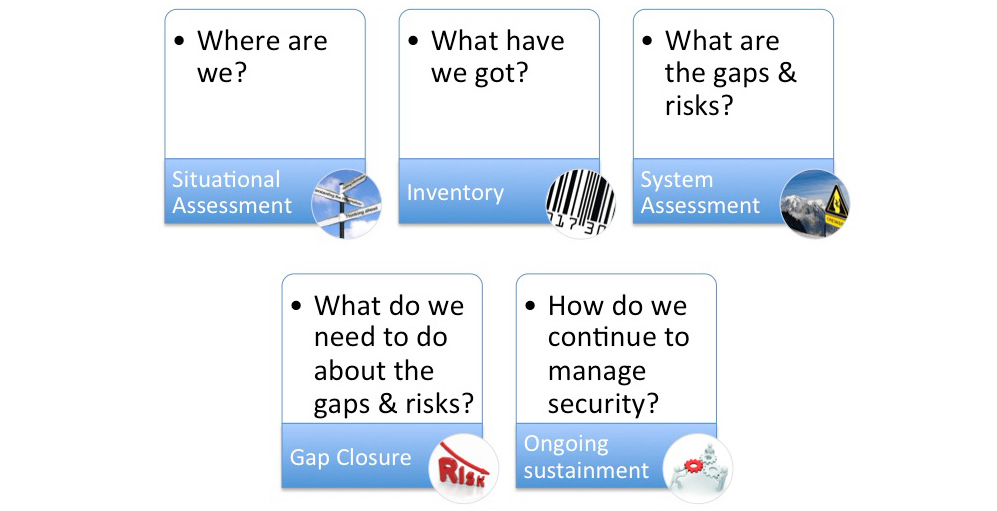
We help organizations with industrial control systems proactively manage the risk of cyber incident using a five-step process:
- Situational awareness - to identify the level of maturity the organization has with respect to cybersecurity
- Inventory - to identify the industrial control system assets and their interconnections and dependencies
- System assessment - to produce a gap analysis that identifies the priority activities to manage cybersecurity risk
- Gap closure - to implement actions to close gaps and reduce cybersecurity risk
- Ongoing sustainment - to embed the processes, procedures and organizational culture necessary to maintain good cybersecurity management.


